
Threat Intelligence (TI) is no more a costly subscription to be purchased. Thanks to the open culture drive, multiple big security vendors have made their threat intelligence platform available to all. Today the fact is, there is not dearth of TI information, we are overwhelmed with threat intelligence information and consuming of this wealth of information is like drinking water from a fire hydrant.
Is there an elegant approach to this common challenge?
A highly efficient threat intelligence requires few core tenets:
Threat intelligence enables with strategic, tactical & operational information
Organizations embracing threat intelligence into their cyber security management should understand the larger purpose of threat intelligence and its fitment into their cyber security ecosystem.
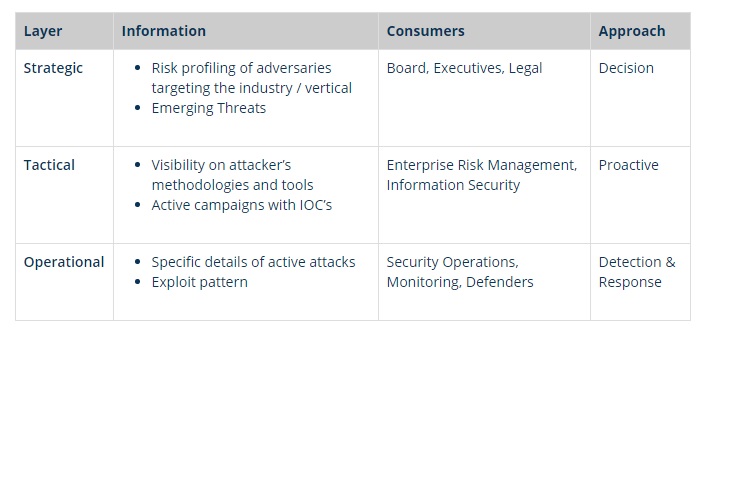
The core objective of threat intelligence is actionable information and insights
The core objective of threat intelligence management is to generate specific actionable information for enabling proactive protection and provide insights into tools, techniques and team behind attacks to security professionals for taking informed decisions as need arises.
Threat intelligence output depends on the accuracy, timing and relevance of the intelligence
Threat intelligence platform should validate the accuracy of the intelligence from multiple sources and the intelligence should be acquired and disseminated in a timely manner. Lastly, the relevance of the threat intelligence to the organization.
Worth of a threat intelligence is based on the source
As part of threat intelligence acquisition, intelligence should feed from diverse sources. Organizations go wrong in assuming threat intelligence is only from external feeds, data feed should be gathered both from internal and external sources below should be minimum which organizations should consider initially.

Capability to identify, track and predict cyberattack using threat intelligence hinges on the platform
Converting a raw threat intelligence into an actionable and valuable insight depends on the effectiveness of the threat intelligence platform, which manages the entire life-cycle of the threat feed. The platform should be agnostic to log type, source and volume, so that the platform effortlessly integrates with existing eco-system and produces near real-time actionable intelligence. The platform should be agile to accept new feeds with as minor changes as possible.
Actionable intelligence to automated action
Comprehensive power of actionable intelligence can be realized only if enforced within a stipulated time. The intelligence could lose its value, if action is not time-bound. For time sensitive intelligence, action should be automated with defined workflow. Few scenarios where automated action can be considered for implementation:

A successfully deployed threat intelligence platform will increase the efficiency of incident handling and reduces time to respond to a threat. It will also increase the preparedness to defend emerging threats and enable insights & context to incidents. TI can also assist risk management team to build threat profiling.
Organizations using threat intelligence effectively elevate their cyber security protection from reactive to proactive.
The author is Head - Cyber Security, IRMC, Wipro

 In
In
Comments
Orlistat Best Price https:/
Orlistat Best Price https://buycialisuss.com/# - Cialis Cerazette Clomid <a href=https://buycialisuss.com/#>Buy Cialis</a> Rogaine Men Over 50
Propecia Discount Pharmacy
Propecia Discount Pharmacy https://agenericcialise.com/ - Generic Cialis Prednisone 10 Mg <a href=https://agenericcialise.com/#>Cialis</a> Entraр“в®nez
Propecia Discount Pharmacy
Propecia Discount Pharmacy https://agenericcialise.com/ - Generic Cialis Prednisone 10 Mg <a href=https://agenericcialise.com/#>Cialis</a> Entraр“в®nez
Propecia Discount Pharmacy
Propecia Discount Pharmacy https://agenericcialise.com/ - Generic Cialis Prednisone 10 Mg <a href=https://agenericcialise.com/#>Cialis</a> Entraр“в®nez
Add new comment