
SMBs that decide to voluntarily inform their stakeholders and the public about a breach, on average, are likely to lose 40% less than their peers that saw the incident leaked to the media. The same tendency has also been found to be the case in enterprises. This finding is from a Kaspersky report, titled How businesses can minimize the cost of a data breach.
Failure to suitably inform the public about a data breach in a timely manner can make the financial and reputational consequences of a data breach more severe. Some high-profile cases include Yahoo!, who was fined and criticized for not notifying their investors about the data breach it experienced, and Uber’s fine for covering up an incident.
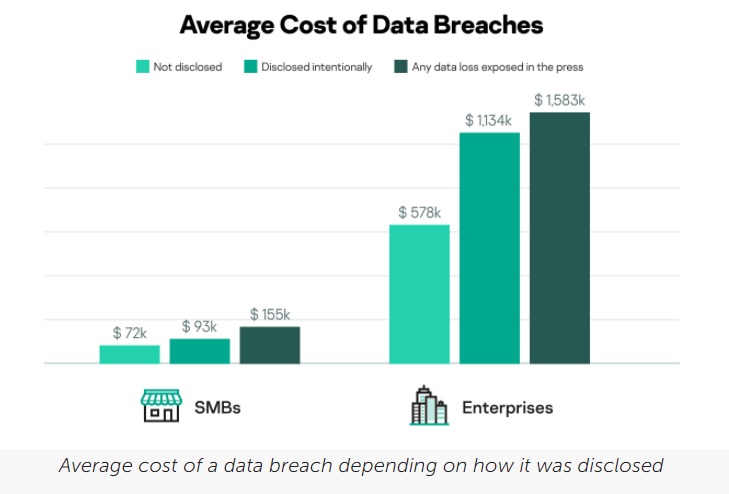
Kaspersky’s report, based on a global survey of more than 5,200 IT and cybersecurity practitioners, shows that organizations that take ownership of the situation usually mitigate the damage. Costs for SMBs that disclose a breach are estimated at USD 93k, while their peers that had an incident leaked to the media suffered USD 155k in damage. The same is the case for enterprises: those that voluntarily inform their audiences about a breach experienced less financial damage (28%) than those whose incidents were leaked to the press – USD 1.134 million compared to USD 1.583 million.
Only around half (46%) of businesses revealed a breach proactively. 30% of organizations that had experienced a data breach preferred not to disclose it. Almost a quarter (24%) of companies tried to hide the incident but saw it leaked to the media.
Although minimal losses were reported by businesses that managed not to disclose the incident, this approach is far from ideal. Such companies are at risk of losing even more if — or more likely when — a cybersecurity incident is revealed to the public against their intentions.
The survey further proved that risks are especially high for those companies that couldn’t immediately detect an attack. 29% of SMBs that took more than a week to identify that they had been breached found the news in the press, which is double those that detected it almost immediately (15%). For enterprises, these figures are similar at 32% and 19% respectively.
“Proactive disclosure can help turn things around in a company’s favor – and it goes beyond just the financial impact. If customers know what happened firsthand, they are likelier to maintain their trust in the brand. Also, the company can give its clients recommendations on what to do next so that they can keep their assets protected. The company can also tell their side of the story by sharing reliable and correct information with the media, instead of publications relying on third-party sources that may depict the situation incorrectly,” comments Yana Shevchenko, Senior Product Marketing Manager at Kaspersky.
To reduce the chance of suffering damaging consequences from a data breach, Kaspersky recommends that businesses follow these recommended actions in advance:
- For enterprise endpoint level advanced threat detection, investigation, proactive threat hunting and fast response, implement EDR solutions such as Kaspersky Endpoint Detection and Response. Smaller companies with limited expertise in cybersecurity can benefit from Kaspersky EDR Optimum which provides basic EDR capabilities, including better visibility into endpoints, simplified root cause analysis and an automated response option.
- In addition to endpoint protection, enterprises should implement a corporate-grade security solution that detects advanced threats on the network, enriched with threat intelligence such as Kaspersky Anti Targeted Attack Platform. It helps to protect from professional cybercriminals who favor a multi-vector approach and often combine many different techniques into a single planned attack.
- To respond in a timely manner to a cyberattack, combine in-house Incident Response team as a first-line of response, and escalate more complex incidents to third-party experts.
- Introduce awareness training for employees to explain to them how to recognize a cybersecurity incident and what they should do if one occurs, including immediately notifying the company’s IT Security department.
- Consider conducting special training for all parties involved in dealing with the aftermath of a data breach, including communication specialists and the head of IT security, such as Kaspersky Incident Communications.

 In
In
Add new comment